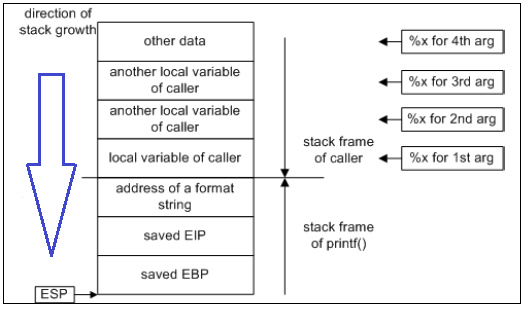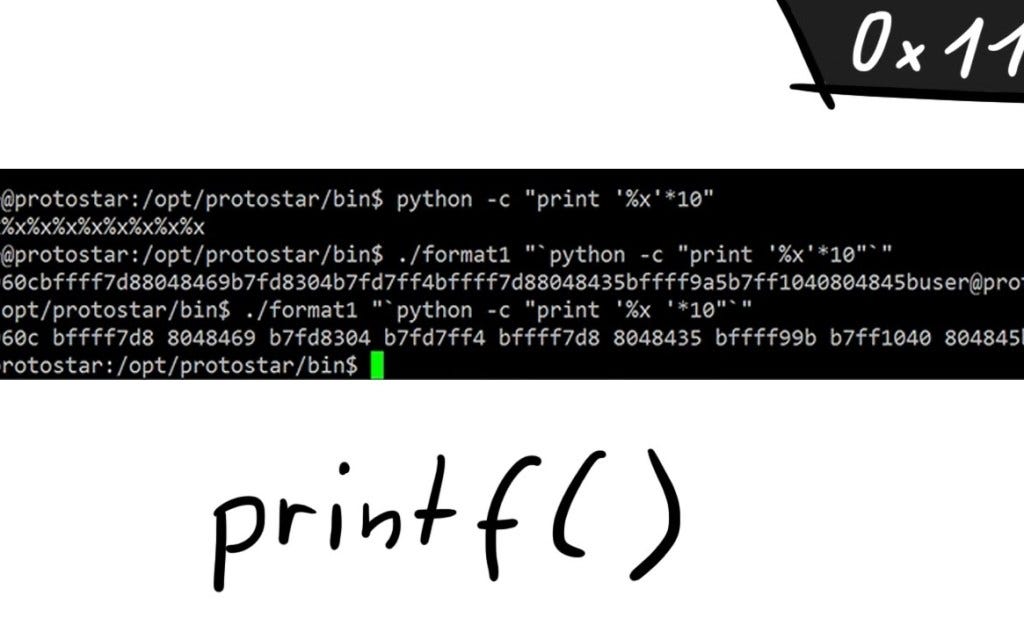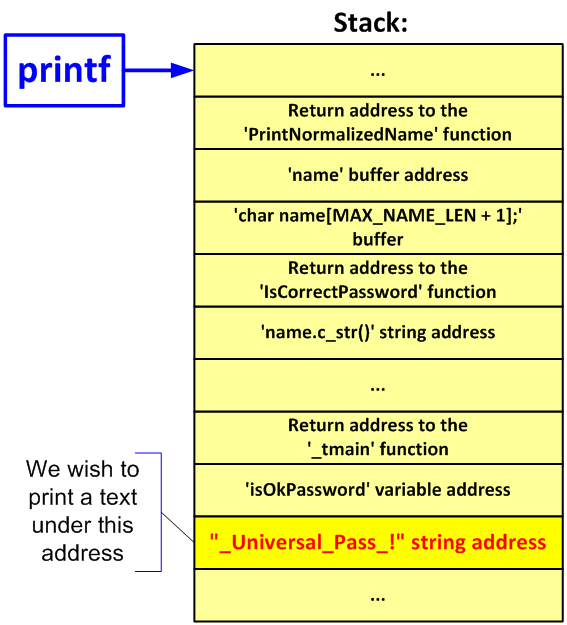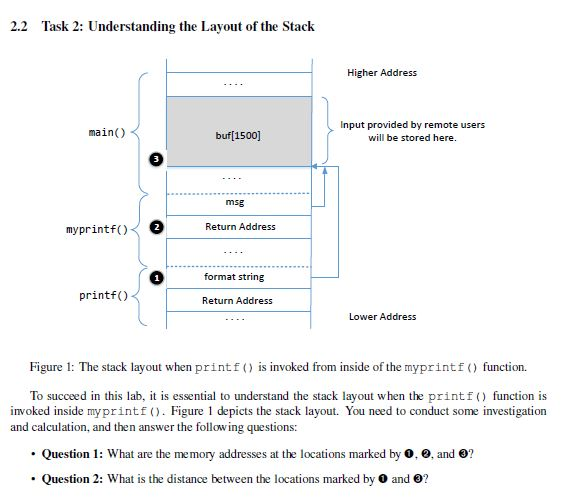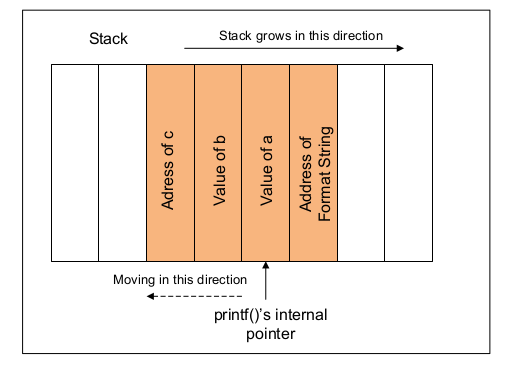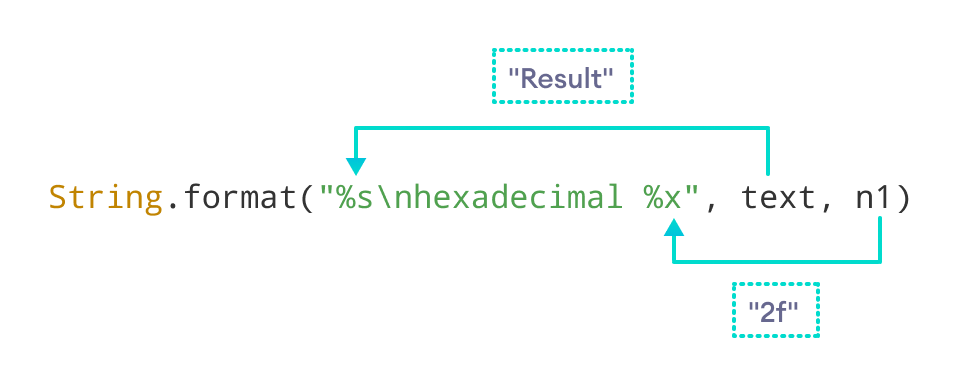
Format string vulnerability. What's a format string vulnerability? | by DanielOrihuela | Jan, 2024 | Medium

Metasploit for Beginners: Create a threat-free environment with the best-in-class tool: Rahalkar, Sagar: 9781788295970: Amazon.com: Books
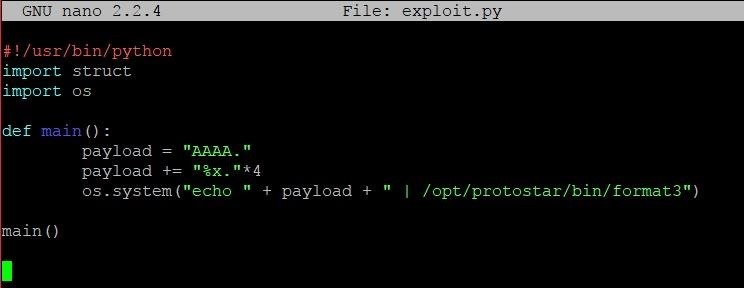
Exploit Development: How to Write Specific Values to Memory with Format String Exploitation « Null Byte :: WonderHowTo

ITS 450 - Solving the Format String vulnerability problem and finding the return address location - YouTube